Tech Corner: Two-Factor Authentication

How often do you check your email, social media, or financial accounts each day? Did you know that your accounts are more vulnerable to cyber-attacks if you have not enabled two-factor authentication?
The Federal Trade Commission (FTC) indicates that consumers should use two-factor authentication to protect all of their accounts, personal, business, and financial.
Employing Two-factor Authentication
Relying solely on passwords to access accounts is similar to having only one lock on a door securing a home. A door secured with a lock and a deadbolt is similar to two-factor authentication, which provides enhanced protection to individuals. Basically, if an individual implements two-factor authentication on their accounts, even if a hacker has access to their username and password, they will not be able to retrieve any information without the second authentication factor.
Common Authentication Methods Several platforms have adopted two-factor authentication and have allowed users to select their preferred method of verification. Some of the most common methods are:
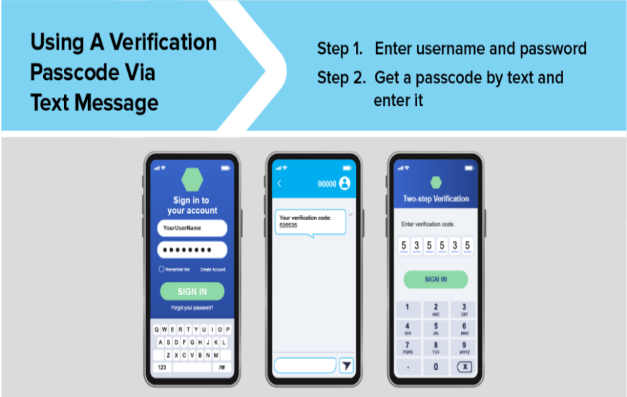
- One-time passcodes,
- This method entails receiving a verification passcode via text message or email. The code typically consists of six digits, is valid for a single log-in attempt, and automatically expires.
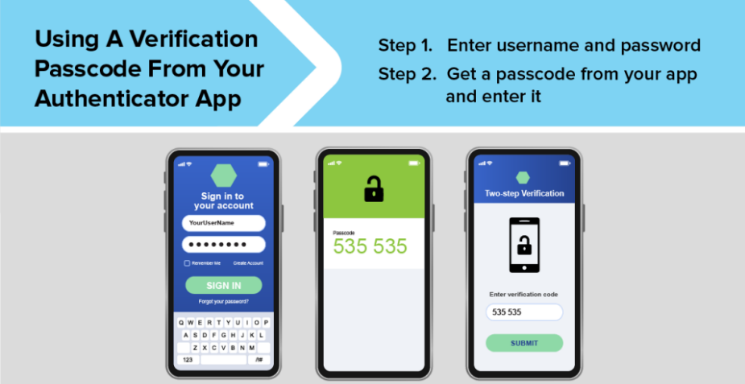
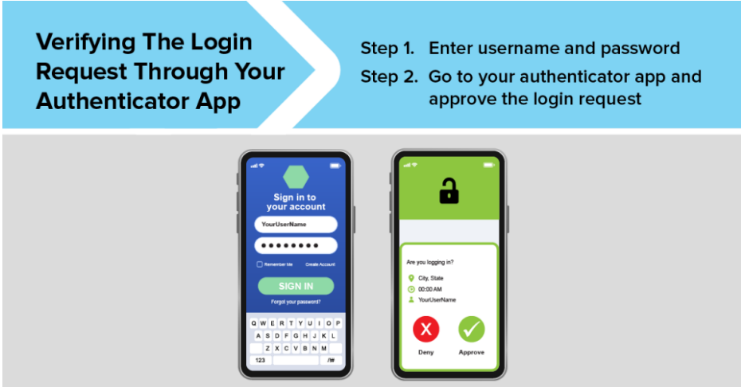
- Authenticator application, and
- An authenticator app offers the possibility of receiving push notifications on your phone or tablet whenever there’s an attempted login to your account. These notifications typically provide details about the login attempt, such as the account being accessed, the geographical location of the attempt, the device type used, and the date and time of the login attempt. You can then approve or deny the request with a simple tap. There are several variations of authenticator apps like Google Authenticator, Microsoft Authenticator, and Duo.
- Security key.
- Security keys are physical devices serving as your secondary authentication factor, available in various forms and sizes. Security keys validate their association with your account. Some security keys plug into a USB port, while others utilize near-field communication (NFC) to establish connection when held close to your device.
The FTC recommends that individuals take a couple of minutes to set-up two-factor authentication on their accounts to prevent spending countless hours on trying to recover lost data or deal with identity theft.
Do you want to know more about keeping your personal information and identity safe? Sign up for Consumer Alerts from the FTC here.